Best Practices for Cyber Security Risk Mitigation

What is Risk Mitigation in Cyber Security?
In today’s digital world, cyber security is more important than ever. With the rapid growth of technology and online platforms, organizations are increasingly vulnerable to cyber threats. As cyber attacks evolve in sophistication, businesses must adopt comprehensive risk mitigation strategies to protect their sensitive data, assets, and reputation. This article will explore the concept of risk mitigation in cyber security, its importance, common risks, and the necessity for businesses to have a proactive approach to security.
What is Risk Mitigation in Cyber Security?
Risk mitigation refers to the process of identifying, assessing, and reducing risks related to cyber threats in order to minimize the likelihood of a security breach. In the context of cyber security, risk mitigation involves understanding the potential threats and vulnerabilities an organization faces and implementing measures to either avoid or reduce the impact of these risks.
The process typically involves several key steps:
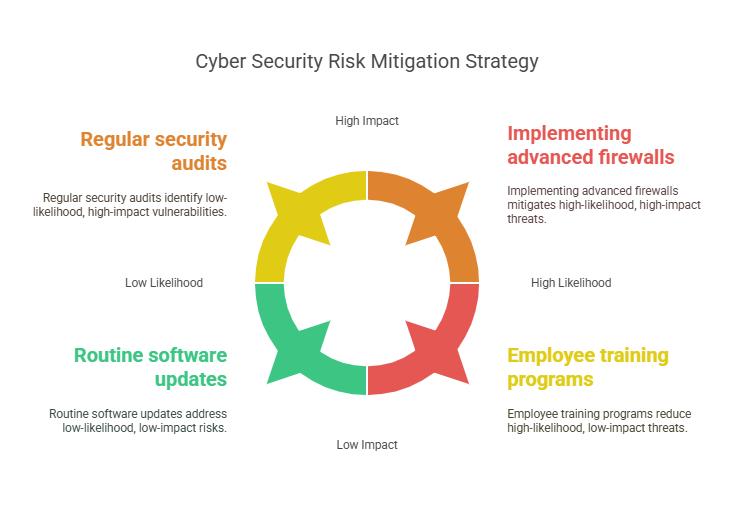
- Risk Identification: This involves recognizing potential vulnerabilities, threats, and the critical assets that need protection.
- Risk Assessment: Evaluating the identified risks by determining the likelihood of their occurrence and the potential damage they could cause.
- Risk Reduction: Implementing controls, policies, and strategies to reduce or eliminate identified risks.
By effectively mitigating risks, organizations can reduce the chances of costly cyber attacks, data breaches, and downtime, ensuring smoother operations and safeguarding their reputation.
The Importance of Risk Mitigation in Cyber Security
Cyber security risk mitigation is vital for several reasons:
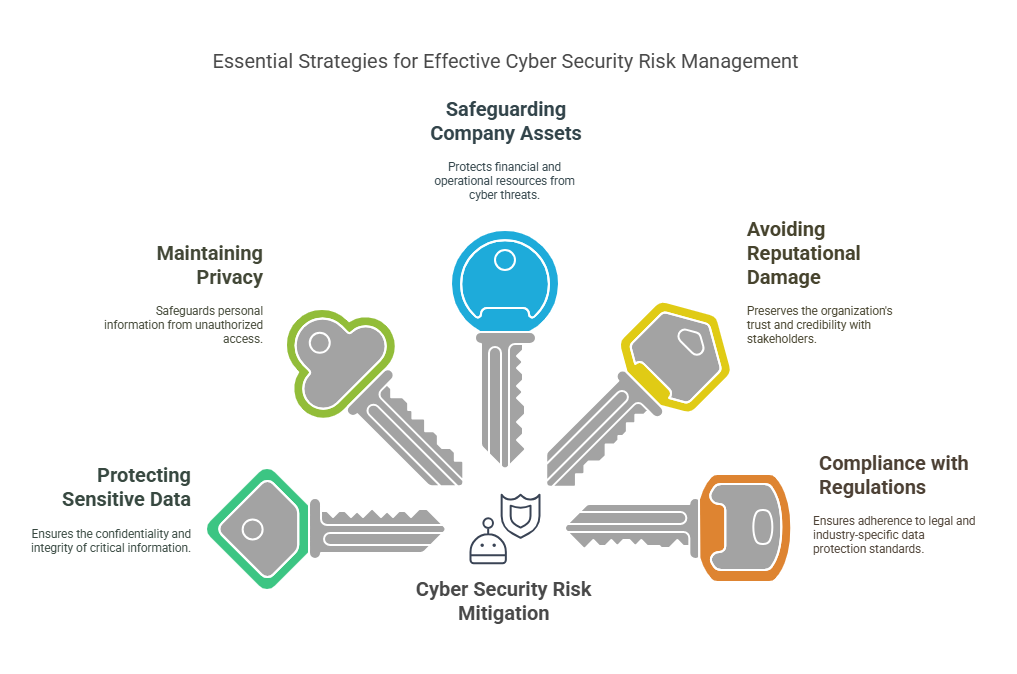
- Protecting Sensitive Data: Organizations often store sensitive information, such as customer details, financial data, and intellectual property. A cyber attack can lead to data theft or exposure, potentially damaging the organization and its clients.
- Maintaining Privacy: Data breaches can result in privacy violations, causing legal repercussions and a loss of customer trust. Mitigating risks helps ensure that data is protected and only accessible to authorized individuals.
- Safeguarding Company Assets: Cyber attacks can lead to financial losses, system downtime, or theft of critical business assets. By mitigating risks, businesses can avoid substantial financial losses.
- Avoiding Reputational Damage: A data breach or cyber attack can severely damage a company’s reputation, resulting in customer loss and decreased trust. Proper risk mitigation measures can help maintain business continuity and a positive reputation.
- Compliance with Regulations: Many industries have stringent data protection regulations (e.g., GDPR, HIPAA) that require businesses to implement certain cyber security measures. Risk mitigation ensures compliance with these legal requirements.
Common Cyber Security Risks
Organizations face a wide range of cyber security threats that can jeopardize their operations. Here are some of the most common risks:
| Cyber Threat | Description |
|---|---|
| Malware | Malicious software designed to damage or gain unauthorized access to systems. |
| Ransomware | A form of malware that locks users out of their systems or encrypts their data until a ransom is paid. |
| Phishing | Fraudulent attempts to obtain sensitive information by posing as a trustworthy entity in electronic communications. |
| Data Breaches | Unauthorized access or disclosure of sensitive information. |
| Insider Threats | Threats posed by current or former employees who intentionally or unintentionally cause harm to the organization. |
| Denial of Service (DoS) Attacks | Overwhelming a system or network with traffic to make it unavailable to users. |
These risks can cause significant harm to an organization, affecting its bottom line, data integrity, and overall security posture.
Why Organizations Need a Cyber Security Risk Mitigation Plan
Developing and maintaining a comprehensive cyber security risk mitigation plan is essential for any organization. Here are a few reasons why:
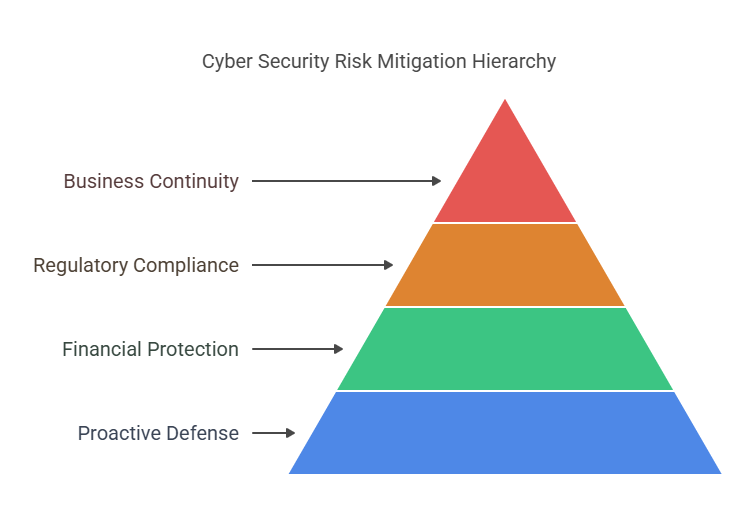
- Proactive Defense: By having a risk mitigation plan in place, businesses can identify and address vulnerabilities before they are exploited by cybercriminals.
- Minimize Financial Losses: Effective risk mitigation strategies help prevent costly data breaches, downtime, and system recovery efforts.
- Ensure Compliance: A solid risk mitigation plan helps businesses comply with industry regulations and avoid legal penalties for non-compliance.
- Business Continuity: By reducing the impact of cyber threats, organizations can maintain operations even during an attack, ensuring minimal disruptions.
How to Implement Risk Mitigation Strategies in Cyber Security
Once an organization understands the importance of risk mitigation in cyber security, the next step is to implement practical strategies to protect against these threats. This section will outline key strategies, tools, and methods to help businesses build and strengthen their cyber security defenses.
Cyber Security Risk Assessment
Before implementing a risk mitigation plan, businesses must first conduct a cyber security risk assessment to evaluate their vulnerabilities and identify potential threats. The process includes:
- Identifying Assets: Begin by identifying all critical assets within the organization, including servers, databases, applications, and sensitive data.
- Identifying Threats and Vulnerabilities: Consider both external and internal threats, such as hackers, malware, and insider threats, as well as system vulnerabilities, such as outdated software.
- Assessing Likelihood and Impact: Evaluate the likelihood of each risk occurring and the potential impact it would have on the organization.
- Prioritizing Risks: Based on the likelihood and impact, prioritize the risks that need immediate attention and mitigation.
Developing a Risk Mitigation Strategy
Once the risk assessment is complete, organizations should develop a clear cyber security risk mitigation strategy. Key components of this strategy include:
- Setting Goals: Define specific objectives for mitigating cyber risks, such as reducing the chance of a data breach or enhancing employee security awareness.
- Defining Risk Tolerance: Determine the level of risk that the organization is willing to accept, considering both the likelihood of threats and the potential impact.
- Selecting Mitigation Techniques: Choose the most appropriate techniques and tools to mitigate the identified risks. This may include technology solutions, policies, procedures, and employee training.
Risk Mitigation Techniques and Tools
There are several risk mitigation techniques and tools available to organizations. Here are some of the most effective methods:
- Firewalls and Antivirus Software: Firewalls act as barriers between internal systems and external threats, while antivirus software helps detect and block malicious programs. Both are essential for preventing malware attacks.
- Encryption: Encrypting sensitive data ensures that even if data is intercepted or accessed by unauthorized individuals, it remains unreadable and protected.
- Regular Software Updates and Patches: Cybercriminals often exploit known vulnerabilities in outdated software. Regular updates and patches ensure that systems are protected against the latest threats.
- Employee Training and Awareness: Human error is often the weakest link in cyber security. Training employees to recognize phishing attacks, use strong passwords, and follow proper security protocols can greatly reduce the risk of successful cyber attacks.
- Multi-Factor Authentication (MFA): Implementing MFA adds an extra layer of security by requiring users to provide two or more forms of authentication (e.g., a password and a biometric scan) before gaining access to critical systems.
- Incident Response and Recovery Plans: It is essential to have a response plan in place for quickly addressing security breaches. This includes clear protocols for identifying, containing, and recovering from cyber attacks to minimize damage.
Role of ExactBackgroundChecks in Cyber Security Risk Mitigation
ExactBackgroundChecks provides an additional layer of security by helping businesses reduce risks related to insider threats. By conducting thorough background checks on new hires, organizations can identify potential risks, such as employees with a history of unethical behavior or criminal activity. This can help prevent data breaches or internal misconduct from employees, further enhancing the organization’s overall security posture.
Legal Aspects of Cyber Security Risk Mitigation
Organizations must understand the legal implications of cyber security, as non-compliance with regulations can lead to significant penalties. Below are key legal considerations:
- Data Protection Regulations: Many countries have implemented strict data protection laws, such as the General Data Protection Regulation (GDPR) in the European Union, the California Consumer Privacy Act (CCPA), and the Health Insurance Portability and Accountability Act (HIPAA) in the U.S. These regulations require businesses to safeguard personal data and take proactive steps to prevent cyber attacks.
- Compliance with Industry Standards: Adhering to industry standards such as ISO 27001 (information security management), NIST (National Institute of Standards and Technology), and PCI-DSS (Payment Card Industry Data Security Standard) helps organizations maintain best practices for cyber security.
- Legal Liability in the Event of a Cyber Attack: If a business fails to properly mitigate cyber security risks and suffers a breach, it may be held legally liable for damages. This could result in hefty fines, lawsuits, and loss of customer trust.
Frequently Asked Questions (FAQs) about Risk Mitigation in Cyber Security
What is risk mitigation in cyber security?
Risk mitigation in cyber security is the process of identifying, assessing, and reducing cyber threats to minimize the likelihood and impact of security breaches.
Why is risk mitigation important for organizations?
It's crucial for protecting sensitive data, maintaining privacy, safeguarding company assets, avoiding reputational damage, and ensuring compliance with data protection regulations.
What are some common cyber security risks organizations face?
Common risks include malware, ransomware, phishing, data breaches, insider threats, and denial-of-service (DoS) attacks.
How can organizations implement effective risk mitigation strategies?
Organizations can implement strategies by conducting risk assessments, developing mitigation plans, using tools like firewalls and encryption, providing employee training, and establishing incident response plans.
What are the legal aspects to consider regarding cyber security risk mitigation?
Organizations must comply with data protection regulations (e.g., GDPR, HIPAA), adhere to industry standards (e.g., ISO 27001, NIST), and understand their legal liability in the event of a cyber attack.
Conclusion
Effective risk mitigation in cyber security is crucial for organizations of all sizes. By identifying threats, assessing risks, and implementing strategies such as firewalls, encryption, employee training, and regular updates, businesses can minimize their exposure to cyber threats. Legal compliance with regulations like GDPR and HIPAA is essential to avoid legal consequences. Partnering with services like ExactBackgroundChecks.com can further enhance security by reducing insider threats. By proactively addressing cyber security risks, organizations can protect their assets, ensure business continuity, and maintain trust with customers.